dubblesort — pwnable.tw
###gathering
around a couple of testing the binary, I found this
first is the weird looking output, of the binary when I input more than 6 characters
second is our thing here, stack smashing !!! now it’s seems like there must be an over flow in side this state
now let’s analyze the pseudo-codes that have been decompiled
first, the binary ask us to input 0x40 bytes, saved it to buffer, then pass %s to the __printf_chk function (with flag args are 1, it means %n can only use in read-only format string), because the buffer variable saved but didn’t zero out the input → leaking the libc address
let’s set breakpoint at __printf_chk
step through it
as you can see, our input didn’t null out at ‘\n’ (0x0a) so it’s continue printing out the rest when meet ‘\x00’ (at 0xffffd004). the above picture show that we leaked 0xf7fb800a and then end with NULL. So it’s mean that we can leak any address in range of buffer(0x40) start at 0xfffcfec.
let’s sum up what do we have until now:
- first, we can leak any address when input name with 0x18 offset
- second, we can arbitrary write at anywhere with the sort
###exploit
with full mitigation and sort function, we can’t use rop to gain shell because the sort function gonna mess up our gadgets, then what can we do? ret2libc !!!
to solve the 1st puzzle we can see that at buffer-0x18, using vmmap to check if there any addr useful to us
ah ha, isn’t that our libc? now we just need to find the libc base address
0xf7fb8000 -0xf7de0000 = 0x1d8000
so 0xf7fb8000 belong to .got.plt . now we can find out the offset of libc challenge
then our libc base addr is
libc_base_addr= leak — 0x1b0000
next is find out /bin/sh and system addr
system = libc_base + 0x3a940
bin_sh = libc_base + 0x158e8bproblem 1 solved !!!
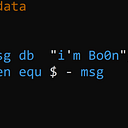
now with problem 2, you probably what to do with the canary, well just one simple character solved it which is non-numeric character like [, ‘, +, -, * …
2nd problem solved!!!
now before we move to exploit, we need to notice a couple things
- our leaked addr which is 0xf7fb800a not actually 0xf7fb8000 so we need to minus 0x0a before moving to the next things
- you have to know that our binary here is sorting, so you must to make sure that our padding stay in the same way as it is, but luckily it seems like our addr lined up already!
because we can arbitrary write the address so let’s find the ret addr of main base on pseudo code (i using IDA to find it quickly) and gdb
idk what’s wrong with my local machine, my script doesn’t work on it but when execute on remote server, welp